Chairman’s Message
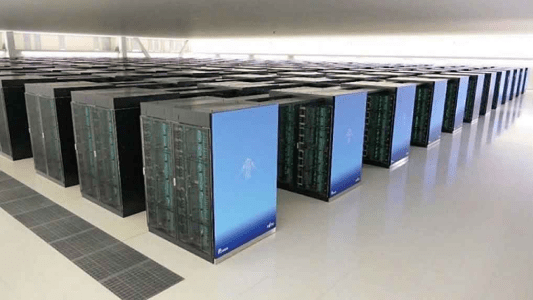
We, NPO OSS Tsukuba Technical Support Center, were established to provide technical support for open-source software (OSS) originating from Japan, centered on the Gfarm file system.
We present the latest development status & contribute with expectations for the future, including actively evolving projects.